>> Alter Solutions is now act digital <<
Cybersecurity Audit & Pentesting services
OT Penetration Testing
Detect security vulnerabilities in industrial environments
Our specialised Pentest team can execute controlled realistic attacks on your Operational Technology (OT) systems and infrastructure to assess their exposure to security vulnerabilities and provide solutions for them.
/1782x1347_ot_penetration.webp?width=1782&height=1347&name=1782x1347_ot_penetration.webp)
What is OT Pentesting?

Operational Technology (OT) Penetration Testing focuses on assessing and identifying security vulnerabilities within industrial environments. This specialised security audit service is primarily used in sectors that rely heavily on Industrial Control Systems (ICS), devices and processes, such as:
- Manufacturing
- Energy
- Oil and gas
- Water and sewage
- Chemical
- Mining
- Transportation
- Telecommunications
- Defence
OT Cybersecurity – and OT Pentesting in particular – is becoming increasingly important given the OT-IT convergence. OT systems that were once isolated, are now more connected than ever to corporate networks and even to the public internet, significantly expanding the attack surface.
OT Penetration Testing with act digital
Our OT security auditors can execute attacks on specific systems and equipment to assess their vulnerabilities. Our services cover a variety of OT components, such as:
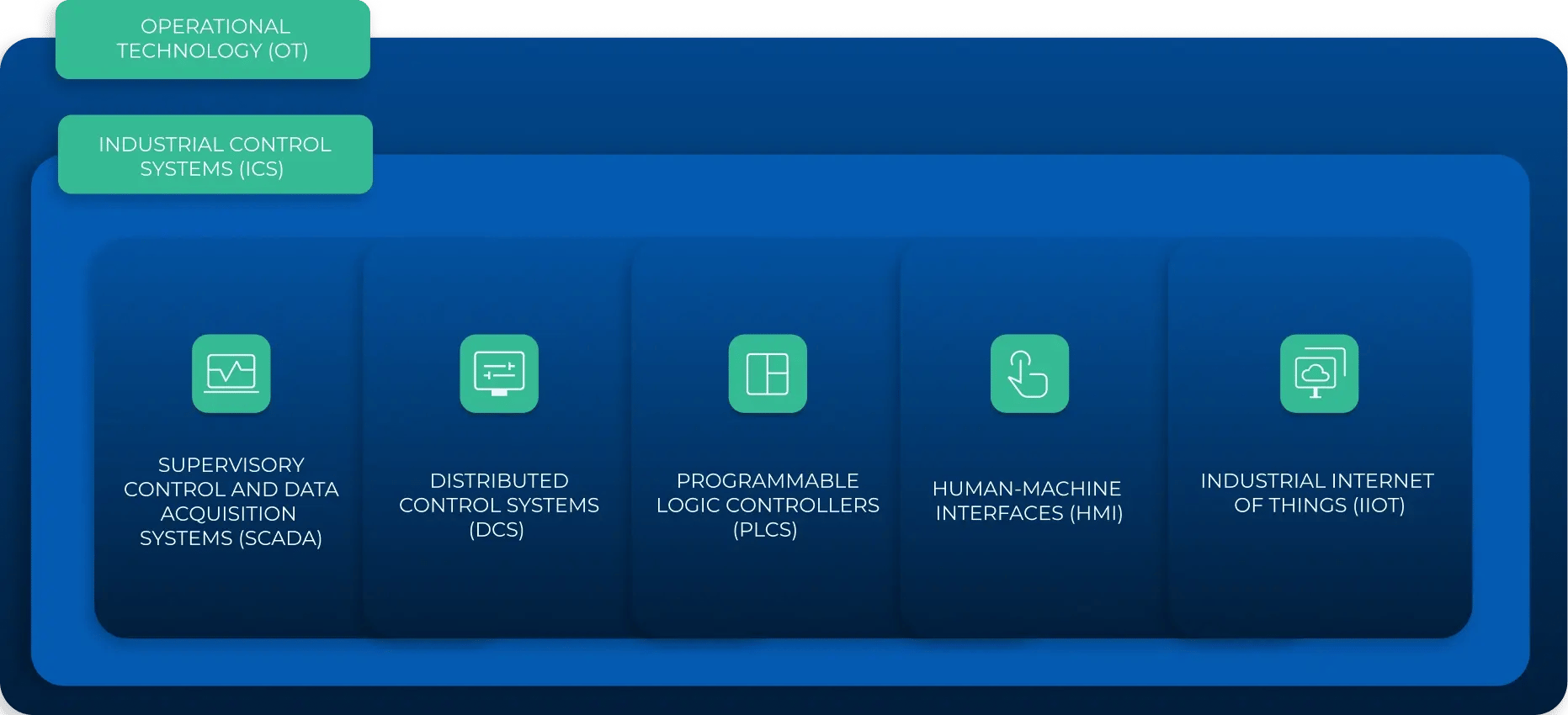
Industrial Control Systems (ICS)
Main components of operational technology, used to monitor, manage and automate industrial processes. They include a variety of devices, systems, and controls like the ones listed below.
Supervisory Control and Data Acquisition Systems (SCADA)
Systems that monitor and manage critical infrastructure processes. They combine software and hardware to collect data in real-time and control equipment remotely. They’re used in most OT environments, for example, in oil and gas pipelines, and water management systems.
Distributed Control Systems (DCS)
Intelligent control systems distributed throughout a facility and used to manage local controllers. They’re typically used in continuous industrial processes like power generation and chemical manufacturing.
Programmable Logic Controllers (PLCs)
Industrial computers that interpret inputs, execute programmed logic, and control outputs based on the given conditions. They are responsible for automation in factories and other industrial environments.
Human-Machine Interfaces (HMI)
Devices or systems that enable human operators to interact with industrial control systems, through graphical or textual displays, buttons, or other input/output methods.
Industrial Internet of Things (IIoT)
Specialised IoT devices designed for industrial applications – also known as Industry 4.0. They enable predictive maintenance, OT asset tracking, and advanced automation in industrial environments.
Our OT Pentesting approaches
You can choose one or even a combination of the following approaches:
Black box Pentest
Penetration testing in “black box” mode emulates an attacker without information on the targeted systems while trying to break into it. This method is very realistic and highlights vulnerabilities that could be exploited by a real attacker, but is not always effective and is considered to risky to be done on critical production environments.
Grey box Pentest
The “grey box” mode is balanced between white and black box pentest. The pentesters have access to a certain level of information about the targeted systems and act as attackers who have already gained some access, in order to conduct more specific tests, while exploring the system further to identify potential vulnerabilities. This method is a good balance between realism and effectiveness, and it can be delivered on critical production environments.
White box Pentest
In this mode, the pentesters have full detailed information about the targeted systems (architecture and system diagrams, source code, access to data, administrative credentials, etc.). This allows them to provide an exhaustive assessment of the system's security status.
The 6 steps of OT Pentesting
When performing an OT Penetration Test for a client, we follow these steps:
#1
Technical discussion to define scope and test scenarios
We begin with in-depth discussion with OT and IT teams to understand the client’s industrial environment’s characteristics, map critical assets and establish relevant scenarios and perimeters to be tested.
#2
Validation of technical requirements
Before initiating the test itself, we validate all technical prerequisites to ensure safe and effective assessment.
#3
Technical testing
Our specialised OT testing team carries out the Penetration Test, employing all the necessary techniques to uncover and evaluate vulnerabilities in the targeted systems or equipment. Throughout the assessment, we maintain continuous communication with the client’s team, notifying them about critical vulnerabilities that require urgent attention, emerging issues, and more.
#4
Live feedback
At the end of the tests and before the report is completed, an "on-the-spot" feedback meeting is held to present to the client the initial conclusions and the list of found vulnerabilities together with the associated recommendations.
#5
Full report delivery
After the test is completed, we provide a detailed report including an executive summary, classifications of all vulnerabilities by level of risk, details on every vulnerability including technical observation, risk assessment and remediation recommendations, among other things.
#6
Closing meeting
Each intervention is wrapped up with debrief session with the client, where we go through the major findings and remediation priorities, clarify technical details, summarise lessons learned, and advise on continuous improvement and assessments.
Why OT Pentesting is vital
Assessing the resilience of industrial environments is beneficial for multiple reasons:
Identifying vulnerabilities in critical systems
OT Penetration Testing reveals security gaps in control systems before attackers can exploit them. This proactive approach helps prevent costly downtime and disruption to critical services and infrastructure such as water systems, transportation networks, or power grids.
Preserving physical safety
By identifying and remediating vulnerabilities in control systems and safety mechanisms, OT Pentesting contributes to reducing the risk of cyberattacks that could cause equipment malfunction or damage, or physical harm to people.
Ensuring regulatory compliance
Critical infrastructure sectors face strict security requirements, making regular OT Penetration Testing essential for demonstrating compliance. By identifying vulnerabilities and security gaps through pentesting assessments, organisations can proactively address weaknesses before regulatory audits, providing documented evidence of their security diligence and helping avoid costly fines and penalties associated with non-compliance.
Securing converging OT-IT environments
As traditional isolated OT systems become increasingly connected to IT networks, this service becomes crucial to identify attack vectors created during this convergence. Our testing methodology addresses threats across both domains and their interconnections.
Preventing financial losses
In many industrial environments, production downtime can cost millions per hour. OT Penetration Testing helps prevent expensive equipment damage and production losses, while reducing liability and insurance costs related to cyber incidents.
Building customer trust
Putting security at the heart of operations by implementing regular OT Pentesting demonstrates commitment to risk management for clients, investors and partners. Ultimately, it’s a way to protect brand reputation that could be severely damaged by security incidents.
OT Cybersecurity in numbers
83%
Percentage of OT leaders that experienced at least one security breach in the past 3 years.
Source: SANS 2024 ICS/OT Cybersecurity Report
62%
Percentage of OT security budgets that are being increased.
Source: 2024 State of Operational Technology and Cybersecurity
25%
Percentage of industrial organisations that had to shut down operations due to a cyberattack in 2023.
Source: Palo Alto Networks’ The State of OT Security 2024
We are certified





act digital is a qualified Information Systems Security Audit Provider, a certification issued by the French National Cybersecurity Agency (ANSSI), one of the most prestigious cybersecurity authorities in Europe.
This certifies the competence and reliability of our auditors to carry out security audits for all scopes:
-
Organisational and physical audit
-
Architecture audit
-
Configuration audit
-
Code audit
-
Penetration Testing (Pentesting)

Other Cybersecurity Audit and Pentest services
Why act digital?
18 years of experience
act digital in Europe was founded in Paris, in 2006, and has since focused on digital transformation. We operate in 12 countries across Europe, America and Africa, and we have been security partners for companies in the manufacturing, service, finance, insurance, transport, and technology sectors for over 10 years.
Flexibility and customer-centric approach
We provide a level of service tailored to the client's needs, going all the way to a 24/7 protection. We have a strong track record across different sectors and technologies, and our approach to IT services is technology agnostic – what's right for each customer is what counts.
Privacy as a core value
Both yours and your customers’ data is safe with us. Our experts operate within the European Union (EU), meaning we fully comply with the General Data Protection Regulation (GDPR).
Key certifications
We hold relevant security certifications like PASSI, ISO 27001, and CSIRT. Our experts are also certified with OSCP, OSCE, GXPN, and CRTM. Plus, we are part of the cybersecurity community InterCERT France.
Our Articles
Contact us today
Fill in our contact form and our dedicated cybersecurity team will get back to you within 24 hours.





